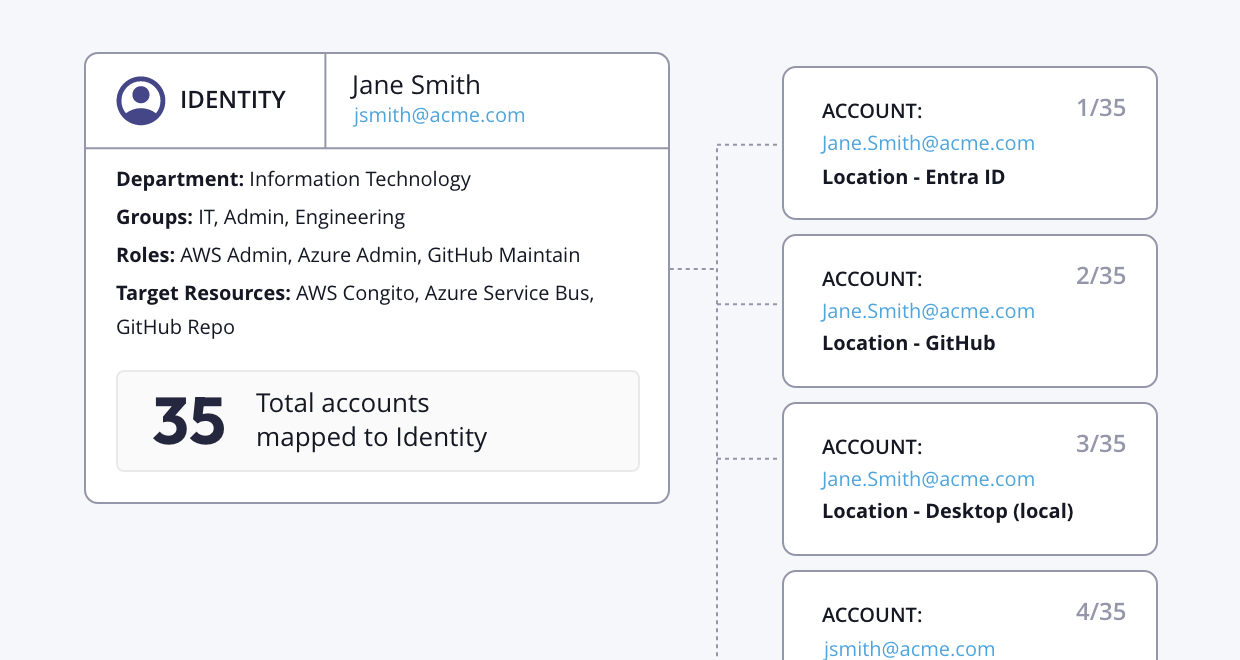
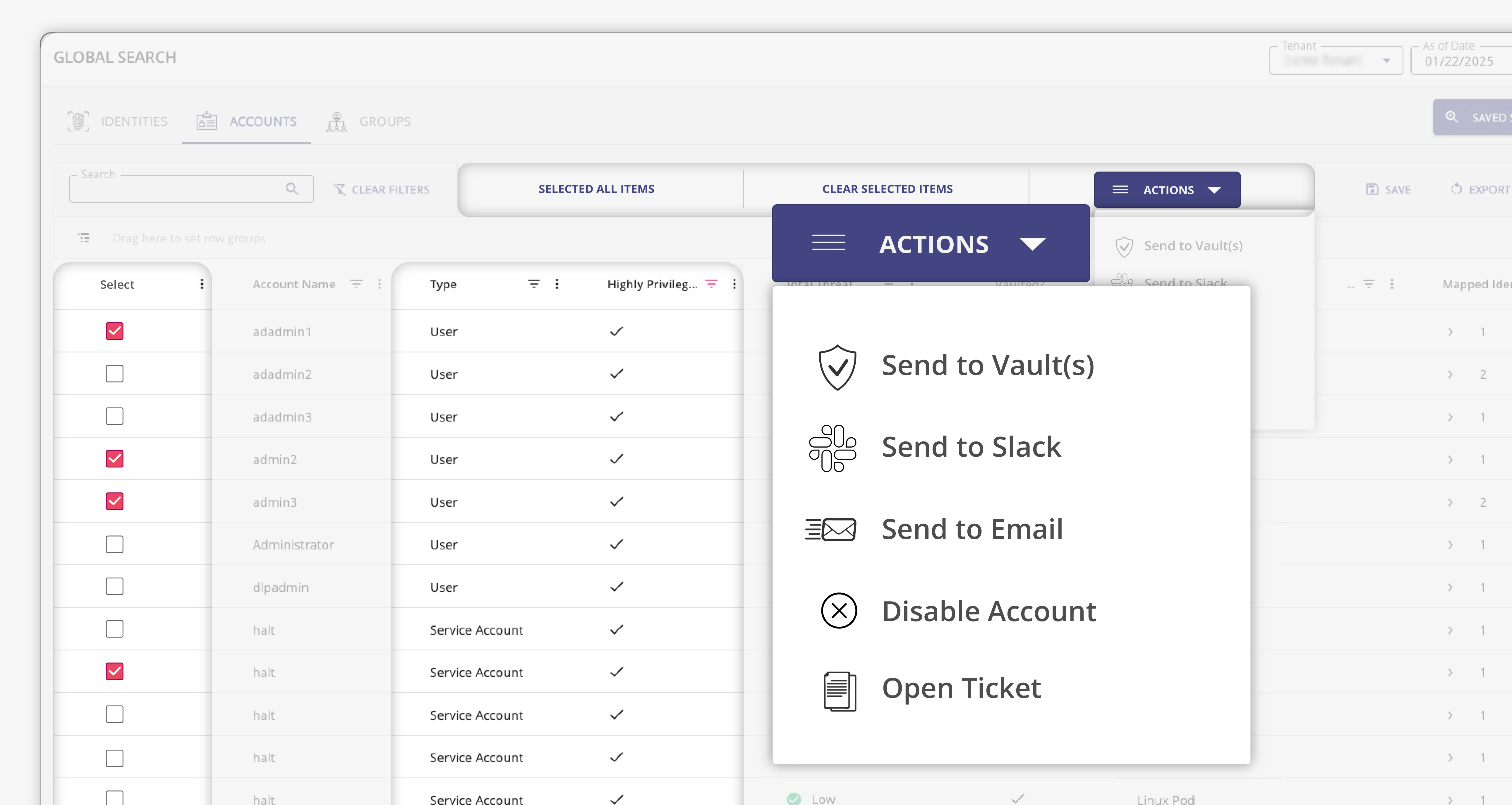
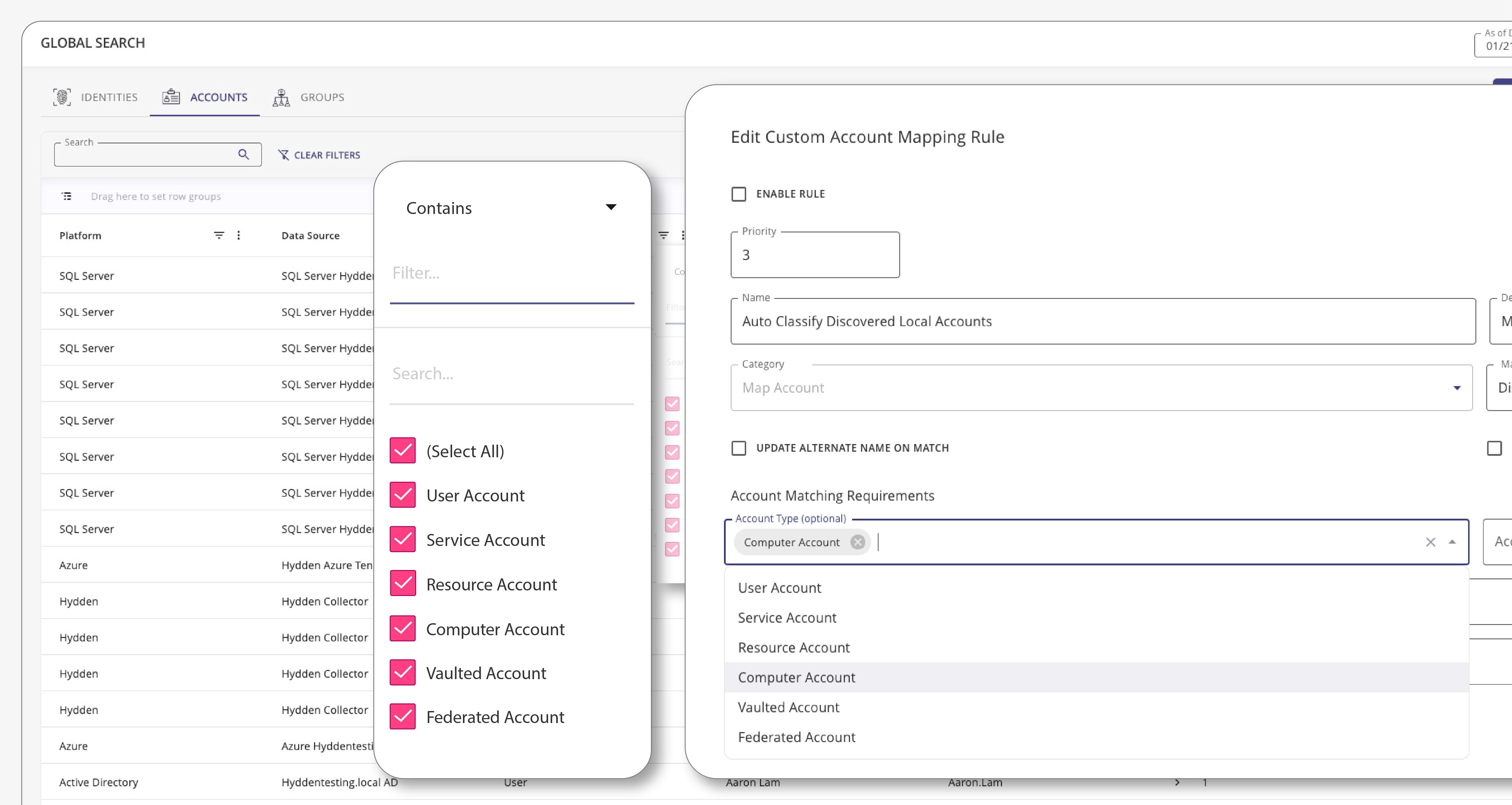
Legacy PAM tools do not scale to meet the demands of today’s infrastructure, systems and applications. Modern PAM tools require real-time data to better inform contextual-based access policies that require granular access control. With Hydden’s identity data layer, attain total coverage of your most critical privileged human and machine identities across every on-premise or SaaS infrastructure, application and system to ensure dynamic and agile control. Take remediating action by adding identities directly to your secrets manager.
PAM
Privileged Access Management
Problem
Account discovery processes in existing solutions were not built to scale to meet the realities of today’s complex corporate identity environment.
Risk
Infrequent or incomplete discovery jobs leave you with unmanaged privileged credentials that are not centrally stored in a vault.
Solution
A mature PAM solution captures every account, authorization change, and access event in real-time to ensure every privileged account is managed.
Hydden’s Privileged Access Management (PAM) solution integrates with your vault to ensure every privileged identity is securely managed
Guarantee New and Updated Accounts are Securely Managed by Your PAM Policies
Discover and manage any machine account type: Service accounts, RPA automation accounts, system accounts, and application accounts. Integrate any authentication method (API keys, security keys, tokens, certificates, cookies) with your PAM solution to rotate these secrets and ensure all machine identities are securely managed.
Get smarter, easier, faster identity security
See how you can gain control over your identity attack surface and proactively manage risks.