Mergers and acquisitions (M&A) significantly increase the complexity of IT systems, as both organizations undertake projects to integration and rationalize technologies. In order to create a centralized identity security foundation that will allow the combined business to move faster towards their strategic goals, security teams must utilize enhanced monitoring and analytics capabilities to identify potential threats and risks.
Merger & Acquisition
Technology Consolidation
Problem
Risk
Solution
Challenges Consolidating Technology From M&A
.
Consolidating technology during mergers and acquisitions involves blending different systems, security, and cultures while keeping operations smooth and secure. Key strategies include:
-
Map Identities: Use advanced tools to scan and map all identities across systems for clear integration insights.
-
Safe Migration: Move systems in phases with risk analysis to reduce security threats.
-
Align Compliance: Unify regulations, policies, and standards across merged systems.
-
Bridge Systems: Create flexible integration for sharing data across diverse tech.
-
Manage Change: Form teams to handle technical, human, and organizational challenges.
Confidently plan, prioritize, and implement technology consolidation projects from M&A
Prioritize Consolidation Based on Risk and Hygiene
Baseline and compare the identity implementations and configurations of the parent company against the company being acquired to determine what is required to create the optimal consolidation and integration strategy.
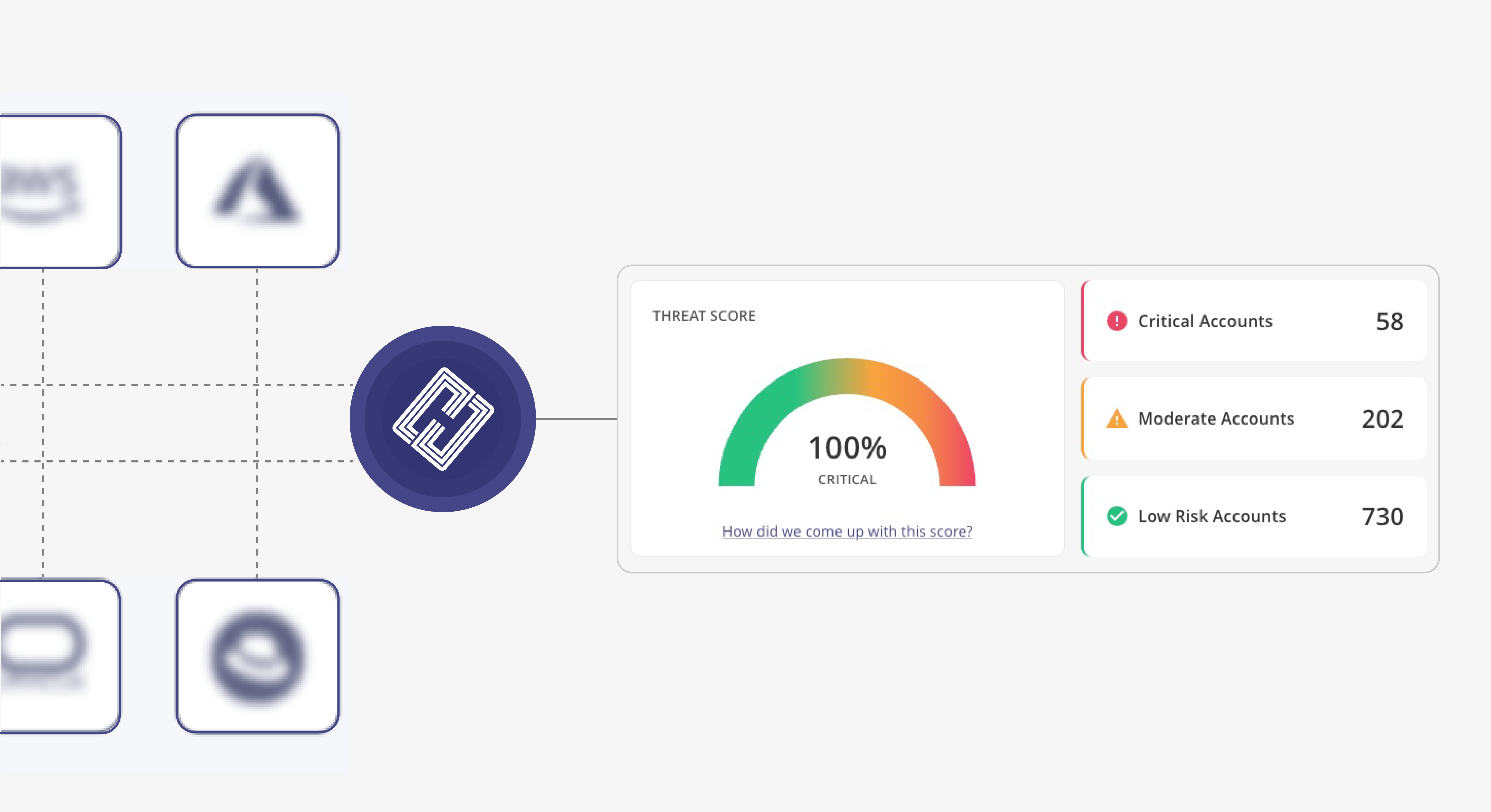

Manage Every Identity’s Access Rights
Monitor and manage accounts on every system across both organizations to ensure departing employees have been removed or group membership is changed for employees in new roles.
Build a Strong Foundation From the Start
Prevent account sprawl by discovering orphaned, dormant, and shadow accounts that inadvertently have access rights to sensitive systems and resources in applications.

Get smarter, easier, faster identity security
See how you can gain control over your identity attack surface and proactively manage risks.


