Identity data is fragmented due to PAM and IGA platforms each having their own processes to discover and manage accounts, resulting in inconsistent information that is often stale and incomplete. Hydden accelerates identity modernization by providing a unified identity data layer that serves as the source of truth across your entire security stack, ensuring clean, enriched identity data with guaranteed integrity for maximum ROI from your existing security controls.
Mature Existing
IGA & PAM Implementations
Problem
Risk
Solution
Identity Modernization Challenges
.
Each PAM and IGA solution maintains its own discovery process, resulting in inconsistent, incomplete, and outdated identity data. This fragmentation creates silos across security teams, breaks automation, and severely limits the ROI from expensive identity controls. Successfully accelerating PAM and IGA implementations involve:
- Eliminate blind spots: Providing visibility into all accounts and entitlements across every system, application, and device.
- Reliable automation workflows: Reliably execute identity processes like provisioning, deprovisioning, and access reviews without failing due to incomplete or bad data.
- Maximizing existing IAM investments: Ensuring all security tools operate with complete, enriched identity data to from every single app.
- Supporting compliance requirements: Confidently demonstrate complete governance over all identities and their access.
Confidently modernize your identity security practices, utilizing Hydden’s flexible API and connector framework to connect to any legacy and custom system
Rapidly connect and onboard all applications
Utilize Hydden’s modern connector framework to quickly and easily connect all your sources. Instead of spending weeks onboarding each application to your IGA platform, our generic connector framework will instantly connect, normalize and enrich data to be safely utilized by your IGA solution.
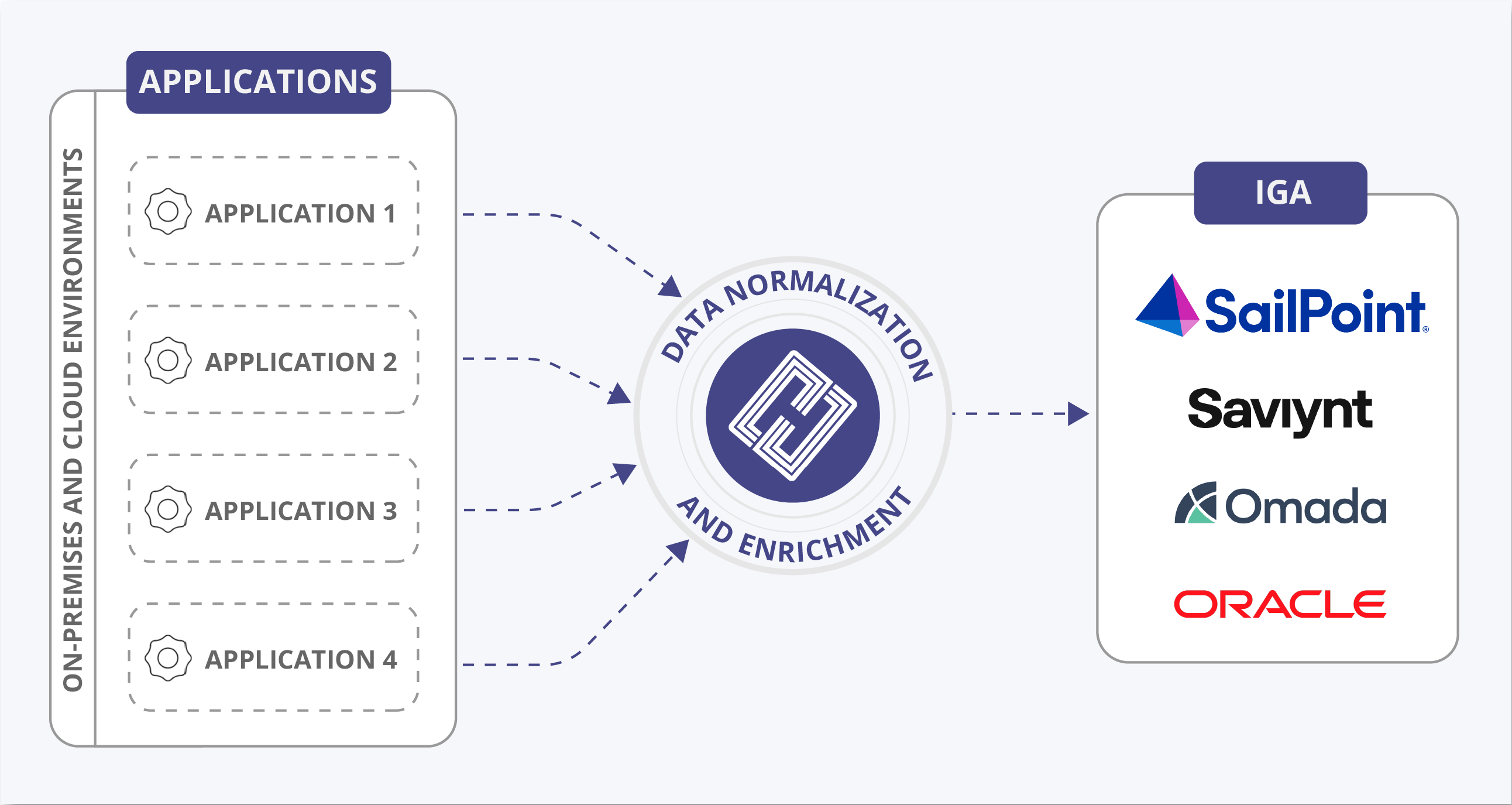

Gurantee Identity Data Integrity
Ensure IGA and PAM solutions are correctly collecting all entitlements (even when the datasource has changes or upgrades) and have an auditable and robust process to make sure the data transmission and extraction of account data happens successfully every time.
Get more ROI out of your identity security investments
Utilize existing identity solution to take remediating action to resolve detected threats, like add missing accounts to your PAM vault and verifying every single account is routed through IGA policies.

Get smarter, easier, faster identity security
See how you can gain control over your identity attack surface and proactively manage risks.


