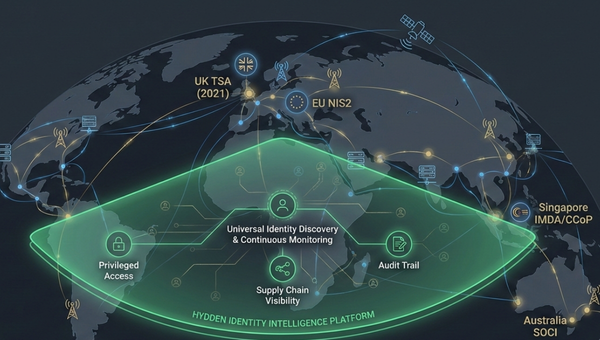
Over the past five years, telecom security regulation has shifted from guidelines to mandates. The UK’s Telecommunications Security Act, the EU’s NIS2 Directive, and Australia’s SOCI framework impose specific identity governance and privileged access control requirements, with significant penalties for non-compliance.
The challenge for CISOs and IAM leaders is that traditional identity tools weren’t built for telecom complexity. Legacy systems, network equipment, cloud platforms, and third-party vendor access often sit outside IGA and PAM coverage. Regulators now expect visibility into all of it.
Below, we examine the major telecom security regulations by region and what it takes to achieve compliance when your current tools only see part of the picture.
The UK Telecommunications Security Act Set the Global Standard
The UK’s Telecommunications (Security) Act 2021 (TSA) is the most comprehensive telecom-specific cybersecurity regulation to date. Passed in November 2021 with enforcement beginning October 2022, the TSA and its accompanying Code of Practice establish detailed technical requirements across network architecture, data protection, supply chain management, and identity security.
Core Identity Requirements Under the TSA Code of Practice
The Code of Practice introduces the concept of “security critical functions” and “network oversight functions,” which are components whose compromise would materially impact network operations. These functions require enhanced protection, and identity security is foundational to that protection.
Privileged Access Management requirements include:
- Privileged access must be temporary, time-bounded, and based on a ticket associated with a specific purpose
- Administrators cannot grant themselves privileged access to the network
- Open tickets must be updated daily documenting why privileged access remains required
- All privileged sessions must be logged, monitored, and retained for audit
Identity Governance requirements mandate:
- Verification of identity before granting privileged access
- Enforcement of least privilege principles across all access
- Continuous monitoring for anomalous access patterns
- Regular access reviews and certification processes
- Complete audit trails of access changes
Third-Party Access controls require:
- Documented shared responsibility models with all suppliers
- Robust audit powers for ongoing monitoring of supplier access
- Segregation of third-party management environments
The Code of Practice explicitly states that providers should establish the principle of “assumed compromise.” This means organizations should operate as if network oversight functions are already subject to undetected attacks, implementing practices that make it difficult for attackers to maintain covert access.
Similar Regulations Worldwide
The UK’s approach is not isolated. Governments worldwide are implementing comparable frameworks, creating a convergent regulatory landscape for telecom providers operating across borders.
European Union: NIS2 Directive
The NIS2 Directive significantly expands cybersecurity requirements for essential entities, a category that explicitly includes telecommunications providers. Telecommunications providers face particularly stringent requirements as “essential entities” subject to the directive’s most rigorous security measures. The Critical Entities Resilience Directive (CERD) extends these requirements to physical and operational resilience.
Australia: Security of Critical Infrastructure (SOCI) Act
Australia’s telecommunications security framework has evolved through the Telecommunications Sector Security Reforms (TSSR), now streamlined into the Security of Critical Infrastructure Act. The Australian government has been particularly focused on 5G security, issuing explicit guidance about high-risk vendor technology and requiring carriers to demonstrate they can adequately protect networks from unauthorized access or interference.
Singapore: Cybersecurity Act and Telecommunications Codes of Practice
Singapore combines the Cybersecurity Act with sector-specific Telecommunications Cybersecurity Codes of Practice issued by the Infocomm Media Development Authority (IMDA). Critical information infrastructure owners, including telecommunications providers, must comply with requirements covering security incident management, threat prevention, and access controls. The Cybersecurity Code of Practice for Critical Information Infrastructure (CCoP2.0) requires organizations to limit access based on roles and context, apply risk-based security measures, and centralize access policies across hybrid environments.
The Identity Security Challenge in Telecommunications
These regulations share a common recognition: identity is the primary attack vector, and identity security is foundational to telecom resilience. But telecommunications providers face unique challenges in achieving the visibility and control these frameworks require because their environments are characterized by:
Massive scale: Major providers operate tens of thousands of network elements, applications, and systems across legacy, virtualized, and cloud-native infrastructure.
Heterogeneous technology: Networks combine decades of legacy equipment with cutting-edge 5G infrastructure, each with different identity management capabilities.
Distributed operations: Global footprints span multiple jurisdictions, data centers, and edge locations, each requiring consistent identity governance.
Complex supply chains: Third-party vendors, managed service providers, and contractors require access to critical systems, often with their own identity stores and access patterns.
Continuous change: Network evolution, M&A activity, and transformation programs create constant identity sprawl that traditional tools struggle to track.
Where Traditional IGA and PAM Fall Short
These regulations require complete visibility into all access, but traditional Identity Governance and Administration (IGA) tools typically see only 20-30% of actual access due to limited connectors. Legacy systems, network equipment, cloud platforms, and development tools often fall outside IGA coverage entirely. Similarly, Privileged Access Management (PAM) tools excel at securing known privileged accounts but struggle to manage accounts outside Active Directory, local accounts, and service accounts embedded in applications.
Top PAM and IGA providers like CyberArk provide robust session management, credential vaulting, and just-in-time access controls, but effectiveness depends on knowing which accounts to protect. The discovery gap is the problem Hydden solves. The TSA’s requirement for “assumed compromise” implies you must know what you’re protecting and you cannot assume compromise of accounts you don’t know exist.
How Hydden Enables Telecom Security Compliance
Hydden’s identity intelligence platform directly addresses the visibility and control gaps that make telecom compliance difficult. Rather than replacing existing IGA and PAM investments, Hydden provides the comprehensive identity data foundation that makes those tools and compliance programs effective.
Universal Identity Discovery
Hydden’s agentless discovery capabilities connect to systems across your environment that traditional tools miss:
- Network Infrastructure: Discover accounts on routers, switches, firewalls, and network management systems regardless of vendor or vintage.
- Legacy Systems: Identify access on mainframes, proprietary platforms, and systems without standard directory integration.
- Cloud and SaaS: Map identity access across AWS, Azure, GCP, and the hundreds of SaaS applications modern telecom operations depend on.
- Development Tools: Gain visibility into GitLab, Jenkins, Kubernetes, and other DevOps platforms where privileged technical access often evades governance.
- Third-Party Access: Identify all vendor and contractor access paths, including shared accounts and service credentials.
This comprehensive discovery directly supports TSA requirements to identify all “security critical functions” and the access paths to them, which is the foundational step regulators expect before you can protect or monitor those functions.
Continuous Access Monitoring
Regulations like the TSA require continuous monitoring for anomalous activity, not just point-in-time reviews. Hydden’s platform provides:
- Real-time change detection: Identify access changes as they happen, not weeks later during manual reviews.
- Anomaly identification: Flag unusual access patterns, privilege escalations, and policy violations automatically.
- Drift detection: Track how access configurations change over time and identify divergence from intended states.
- Third-party activity monitoring: Maintain visibility into vendor access without requiring them to use your PAM tools.
This continuous intelligence enables the “assumed compromise” posture the TSA recommends. You can detect subtle signs of unauthorized access that periodic reviews would miss.
Privileged Account Intelligence
The TSA’s privileged access requirements demand that you know every privileged account, ensure access is temporary and ticket-based, and maintain complete audit trails. Hydden enables this by:
- Discovering unmanaged privileged accounts: Identify local admin accounts, service accounts with excessive privileges, and shared credentials across all systems, not just those integrated with your PAM.
- Mapping privileged access paths: Understand how users can escalate to privileged access, including indirect paths through group memberships, role assignments, and trust relationships.
- Identifying standing privileges: Find accounts with persistent elevated access that should be converted to just-in-time models.
- Supporting PAM integration: Provide the account inventory your PAM solution needs to achieve comprehensive coverage. For CyberArk environments, Hydden identifies privileged accounts that should be vaulted, service accounts that need rotation policies, and access paths that require session isolation.
Access Review Acceleration
Quarterly and annual access reviews consume enormous resources while delivering limited security value, a pain point nearly every CISO recognizes. Hydden changes this by:
- Providing complete access data: Reviews can only be effective if reviewers see all access. Hydden ensures review campaigns include the full picture.
- Enriching with context: Add business context, risk scores, and usage patterns that help reviewers make informed decisions rather than rubber-stamping.
- Automating low-risk decisions: Apply intelligent policies to auto-certify appropriate access while focusing human attention on exceptions.
- Tracking remediation: Ensure revocation decisions are actually implemented across all systems, not just those connected to IGA.
Supply Chain Visibility
The TSA’s extensive third-party supplier requirements demand visibility and control that most organizations lack. Hydden provides:
- Vendor access inventory: Comprehensive mapping of all third-party access paths, including those not provisioned through formal processes.
- Segregation verification: Confirm that third-party management environments are properly isolated as the Code of Practice requires.
- Contract compliance evidence: Generate documentation demonstrating vendor adherence to required security controls.
- Audit support: Provide the detailed access records regulators expect when examining supply chain security.
Working With Your Existing PAM and IGA Investments
Most telecom providers have already invested in privileged access management and identity governance. CyberArk deployments are common across the sector, often driven by compliance initiatives or security programs. Hydden is actively working with telecom providers to extend the value of those investments. Rather than replacing PAM infrastructure, Hydden solves the visibility problem that limits PAM and IGA effectiveness: discovering accounts CyberArk should be managing, providing identity context that informs CyberArk policies, and maintaining visibility where native connectors don’t exist.
Your CyberArk deployment can now protect what matters, not just what it can see. TSA compliance requires demonstrating control over all privileged access to security critical functions. That’s only possible when your controls have complete visibility into the accounts it needs to manage.
Conclusion
The global convergence of telecom security regulations reflects a universal recognition: identity is the attack surface, and identity governance is foundational to resilience. The UK’s TSA, the EU’s NIS2, Australia’s SOCI framework, and Singapore’s cybersecurity codes all demand capabilities that traditional identity tools alone cannot deliver.
Hydden provides the identity intelligence foundation that makes compliance achievable. Not through another point tool that creates its own silos, but through comprehensive visibility that enables your entire security ecosystem to work as intended.
For CISOs navigating these requirements, the path forward is clear: you cannot protect access you cannot see, you cannot govern accounts you don’t know exist, and you cannot demonstrate compliance without complete, trusted identity data.