Identity Security is a complex, multi-dimensional problem, encompassing different teams, processes, technologies, and controls within an organization. This fragmentation often results in silos, breakdowns, and critical gaps that ultimately lead to increased cyber exposure and risk. At Hydden, we think about Identity Security (or Identity and Access Management) through the lens of the Identity Attack Surface.
So what’s Identity Attack Surface Management (IASM)? At its core, IASM is a comprehensive, end-to-end approach of discovering, monitoring, and securing every identity everywhere. IASM requires 100% visibility of every identity – human and machine – and a total understanding of how and when these identities are being used across infrastructure. Which accounts belong to which users? What can those users do within an application? What is the security state of a particular account or group? Have we observed evidence of a compromised identity or another identity attack in progress? These are just some of the questions that IASM helps us answer, which is difficult to address with traditional approaches to IAM, IGA, and PAM.
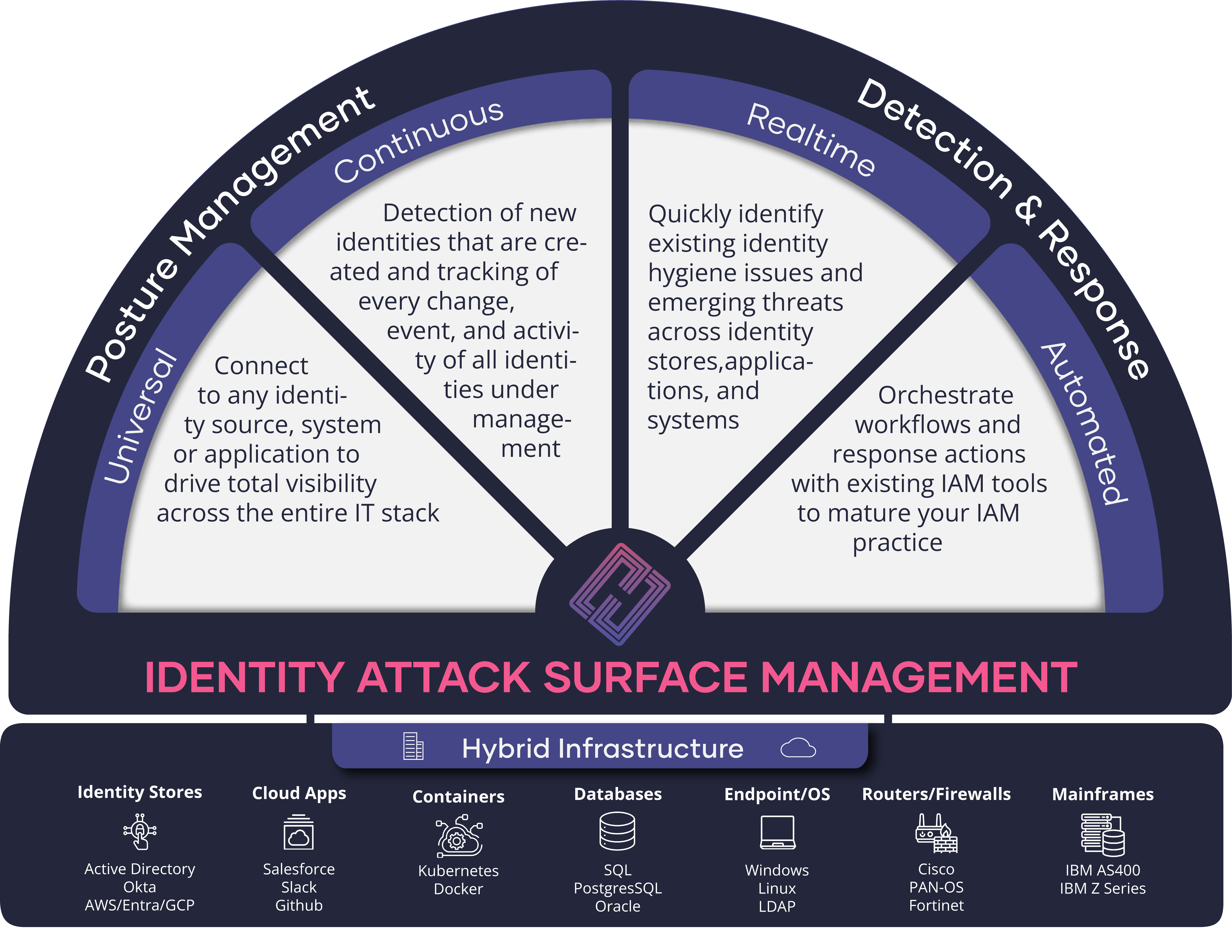 Visibility must extend across your digital and physical estate because identities exist across cloud applications, on-premise databases, on end user laptops and workstations, edge devices like firewalls and routers, and in IoT/OT devices – just to name a few. Just like our laptops have credentials that we use to access our corporate applications, the security teams’ cyber defense tools also have admin portals and user accounts, which are heavily privileged and require much deeper scrutiny and security. Understanding identity security through the lens of the identity attack surface gives security an easier way of thinking about appropriate security controls, processes, and technology components required to safeguard enterprise infrastructure.
Visibility must extend across your digital and physical estate because identities exist across cloud applications, on-premise databases, on end user laptops and workstations, edge devices like firewalls and routers, and in IoT/OT devices – just to name a few. Just like our laptops have credentials that we use to access our corporate applications, the security teams’ cyber defense tools also have admin portals and user accounts, which are heavily privileged and require much deeper scrutiny and security. Understanding identity security through the lens of the identity attack surface gives security an easier way of thinking about appropriate security controls, processes, and technology components required to safeguard enterprise infrastructure.
IASM is an important security paradigm because an enterprise’s identity attack surface is continually expanding. Every new employee, contractor, device (like laptop or workstation) involves the creation of new identities, accounts, and credentials that are entry points to corporate systems and data. More entry points mean more potential access paths that malicious actors can exploit.
Because the identity attack surface is continually expanding, security teams need continuous discovery of every identity to implement effective IASM. Our customers use our platform to drive continuous discovery, risk assessment, and detection of threats across identity infrastructure, and down to systems and applications with local identity stores. Hydden builds an identity data foundation across this infrastructure to provide this top-down, end-to-end view of the identity estate. This makes it easier to search and find information across disparate data sources and automate response actions when potential security issues are detected.
Hydden’s capabilities sit at the nexus of Identity Security Posture Management (ISPM) and Identity Threat Detection and Response (ITDR), providing both proactive recommendations to build a strong foundation and reactive threat detection and response. Both categories are newer yet extremely important developments in the broader IAM market, which has evolved at a lightning pace over the past five years. As identity attacks continue to rise and reap significant damage on companies that lack effective IAM maturity, security teams will need to think about the problem space with this paradigm in mind.
Check out a demo and try Hydden for yourself: https://hydden.com/book-demo/




